Wi-Fi security has significantly improved over the years from initially being more aspirational than real until today, where Wi-Fi 6 security is considered to be on a par with the security of 5G telephony. This FAQ will answer several questions related to Wi-Fi security and encryption: What’s the difference between WEP, WPA, WPA2, and WPA3? What’s the best encryption to use for maximum Wi-Fi speed? And, how does security in Wi-Fi 6 compare with 5G?
What’s the difference between WEP, WPA, WPA2, and WPA3?
The goal of the first Wi-Fi security protocol was to achieve near equivalency with the security of wired Ethernet connections, hence the name Wired Equivalent Privacy (WEP). It didn’t quite work out. WEP uses the Rivest Cipher 4 (RC4) stream cipher for authentication and encryption. Multiple vulnerabilities have been discovered in RC4, rendering it insecure. WEP uses a shared encryption key used by the wireless users and the access points rendering it less secure. Other limitations include:
- WEP does not use efficient encryption algorithms.
- WEP does not authenticate users correctly.
- WEP lacks effective controls over unauthorized data access.
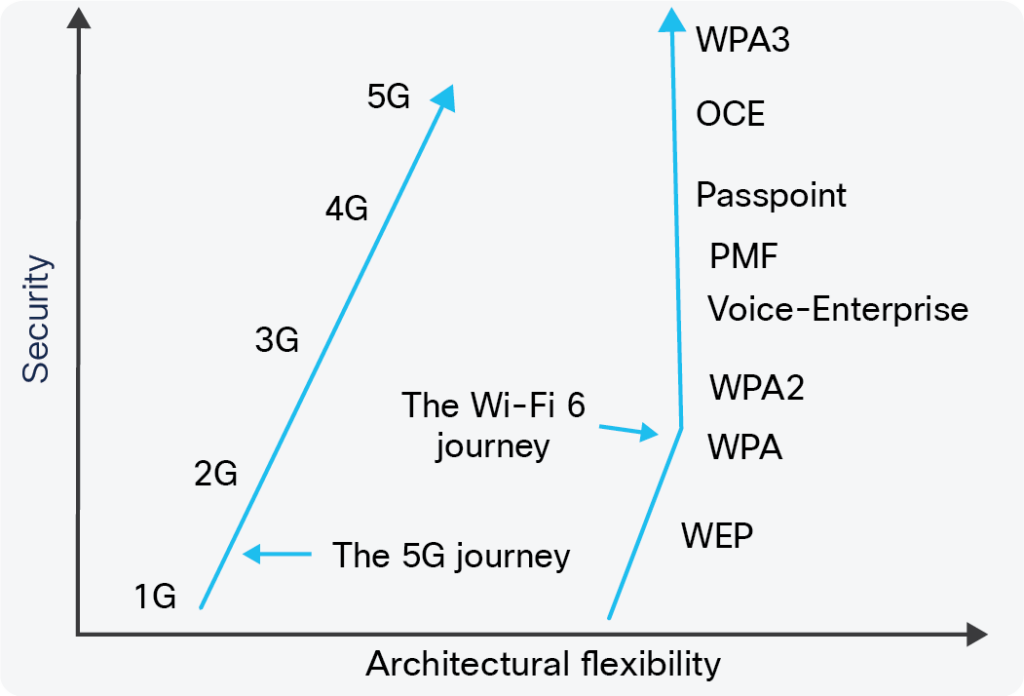
The problems with WEP were so numerous and severe that Wi-Fi protected access (WPA) was introduced as an interim standard for one year. At the same time, WPA2 was being developed as a more advanced security protocol and a long-term replacement for WEP. WPA addressed many flaws of the WEP protocol using stronger encryption, larger encryption keys, and more secure integrity checks. Inherent limitations in both WEP and WPA resulted in the continued development of Wi-Fi security, leading to WPA2 and WPA3 (Figure 1).
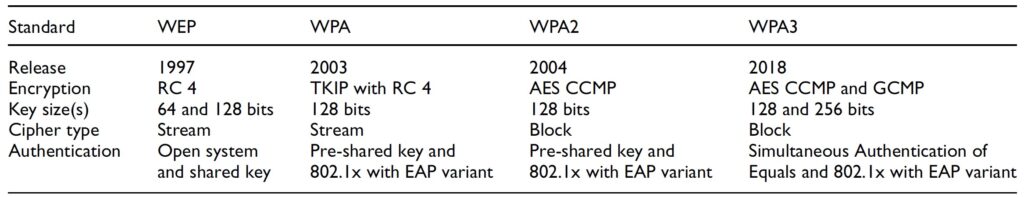
The major similarity between WPA and WPA2 is the 802.1x/Extensible Authentication Protocol (EAP) framework. The major difference is the use of Advanced Encryption Standard (AES) encryption in WPA2. RC4 used in WEP and WPS is a stream cipher, AES is a more secure block cipher. AES uses a 128-bit block size for plaintext and ciphertext, and three different key sizes, 128, 192, and 256 bits, each of which is used in different iterations of the algorithm with a total of 36 iterations used to implement AES. The WPA2 protocol also uses Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP) to replace the less robust Temporal Key Integrity Protocol (TKIP) in WPA.
WPA3 continued the improvements in Wi-Fi security. Despite sharing a common base name with WPA2, WPA3 is inherently different from previous Wi-Fi security protocols. WPA3 is offered in Personal and Enterprise versions. Some of the new features include better protection for simple passwords, encryption for open and personal networks, and more secure encryption for enterprise networks. WPA3 personal and enterprise protocols include encryption based on Simultaneous Authentication of Equals (SAE), replacing the Pre-shared key (PSK) authentication method used in earlier Wi-Fi security implementations. SAE offers much stronger encryption than PSK. WPA3 personal includes encryption on personal wireless networks for each user.
For better protection of wireless networks used for business, WPA3 enterprise has an additional layer of security with a 192-bit key. Another feature included in WPA3 enterprise is Wi-Fi Enhanced Open. With Enhanced Open, conversations between the access points and the wireless hosts in open networks are encrypted with different keys for different connections using Opportunistic Wireless Encryption (OWE). Protected Management Frames (PMF) protect the wireless traffic of management activities between the wireless hosts and the access points.
What’s the best encryption to use for maximum Wi-Fi speed?
WPA2 encryption was designed for speed as well as security. But whether or not it’s faster or slower than WPA3 in actual Wi-Fi networks is a complicated question. While not technically linked, the broad adoption of WPA3 is being enabled by the introduction of 802.ax (Wi-Fi 6). WPA3 certification is not limited to new Wi-Fi 6 devices; WPA3 is also available for many Wi-Fi 5 devices as a software update.
However, it’s not quite that simple. A ‘migration mode’ is defined for 802.11 infrastructure that enables both WPA2 and WPA3 devices to function on the same network. Theoretically, WPA3 is both more secure and faster than WPA2, but the performance can be mixed on networks with both WPA3 and WPA3 devices. A long transition period is expected before purely WPA3 networks become commonplace. Many smart devices such as televisions and IP cameras have longer replacement cycles compared with laptop computers and smartphones. Upgrading smart devices to WPA3 often requires new hardware, not a simple software update. As a result, networks with varying mixes of WPS2 and WPS3 devices will be the norm for an extended period, and so will varying levels of network performance.
How does security in Wi-Fi 6 compare with 5G?
The simple answer is: very well. The same bidirectional authentication capability is used in enterprise-level Wi-Fi 6 and 5G. Specific protocols are not identical but are considered equivalent in terms of security. Enterprise-built Wi-Fi confines key services to local networks, and the networks can control data flow directions. Earlier generations of cellular systems were based on a limited number of outdoor macro base stations. 5G is different and will have orders of magnitude more small base stations, in some cases with a density approaching that of Wi-Fi 6 access points. While that will increase the deployment flexibility of 5G, it will multiply the security risks. As a result, in terms of deployment flexibility and related security needs, Wi-Fi and 5G are moving closer together (Figure 2).
Previous generations of cellular technology relied on SIM cards for user authentication. A single user authentication method is seen to be a hindrance of new 5G use cases such as the industrial internet of things (IIoT) and wireless enterprise access, and 5G integrates the EAP framework developed for Wi-Fi enterprise. The 5G standard shows how to use EAP-TLS certificate-based authentication in 5G and other EAP methods that support mutual authentication. In terms of architectures, Wi-Fi 6 and 5G both rely on four levels of security implementation (Figure 3).
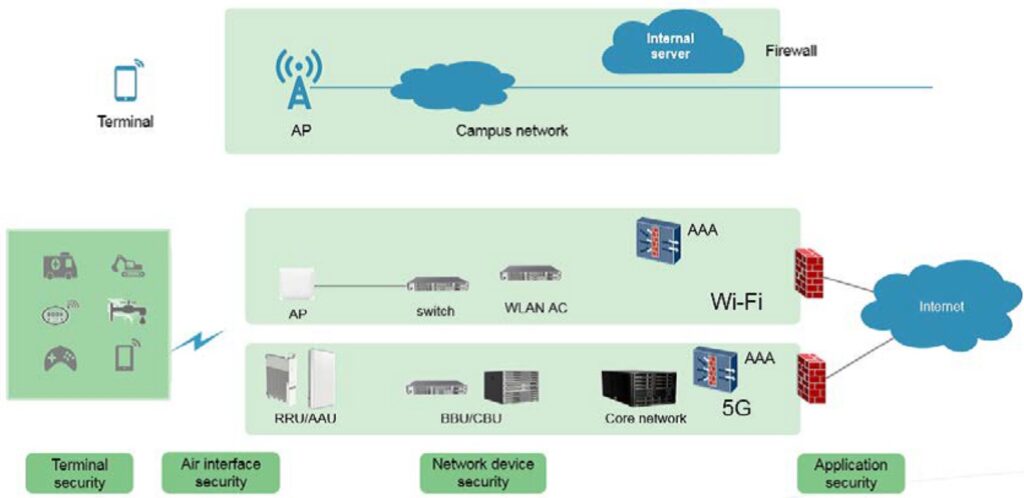
Terminal security – Different types of Wi-Fi terminals require specific security. Network access can be controlled with digital certificates or various identifiers and MAC addresses. Terminal security is a growing concern for 5G, where IoT and IIoT devices must be identified and secured.
Air interface security – Both Wi-Fi 6 and 5G require an AAA authentication server to provide authentication (to identify), authorization (giving permission), and accounting (to create an audit trail). Authorization is based on the authentication of users. User names and passwords (or digital certificates) can authenticate the identities of Wi-Fi 6 terminals. The identities of 5G terminals are authenticated based on the built-in user service identity module. Wi-Fi 6 provides multiple air interface authentication modes such as username/password and digital certificates. 5G provides EAP-AKA-assistant authentication (SIM card), whose security level is generally the same as Wi-Fi 6 air interface authentication modes.
Network device security – The Wi-Fi and 5G standards are of limited usefulness here. The capabilities of IT personnel and the tools available to them are critical in determining network device security. Large enterprises and carriers have the resources to ensure security, while small- and medium-sized enterprises are often more vulnerable due to the limited availability of resources.
Application security – Both 5G and Wi-Fi 6 establish forwarding channels for applications and provide similar levels of security. In the final analysis, application security is more nuanced. The cloud must secure Cloud-based applications. In other instances, the enterprise or local network has some level of responsibility to guarantee the use of only secure applications.
Summary
Security and encryption are important considerations when using wireless networks. The introduction of WPA3 has dramatically improved the security of Wi-Fi. While not explicitly tied together, the adoption of WPA3 in practical terms is being enabled by deploying Wi-Fi 6 devices. Many, but not all, Wi-Fi 5 devices can be upgraded to WPA3 with software updates. It’s expected that mixed networks with WPA3 and WPA2 devices will be commonplace for the foreseeable future, resulting in varying levels of network performance. In terms of deployment flexibility and related security needs, Wi-Fi and 5G are moving closer together; both rely on four levels of security implementation.
References
Educational modules and research surveys on critical cybersecurity topics, International Journal of Distributed Sensors
Examining the Security of Wi-Fi 6 and 5G, Cisco
Security Comparison Between Wi-Fi 6 and 5G, Huawei