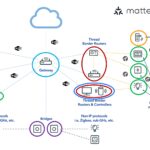
Not elementary particles. The Matter being discussed here is an interoperable application layer software suite for wireless IoT devices. The constituents of that Matter include a modular software stack plus bridges, controllers, border routers, security including authentication, and cloud connectivity. Matter uses Thread, Wi-Fi, Ethernet transport, and Bluetooth LE for commissioning.
Matter was initially called Project CHIP when the Zigbee Alliance started it. Zigbee changed its name to the Connectivity Standards Alliance and continued refining Matter.
This FAQ begins with a dive into the structure and layers in the Matter software stack, followed by discussions of bridges, controllers, and border routers, and closes with a review of Matter security.
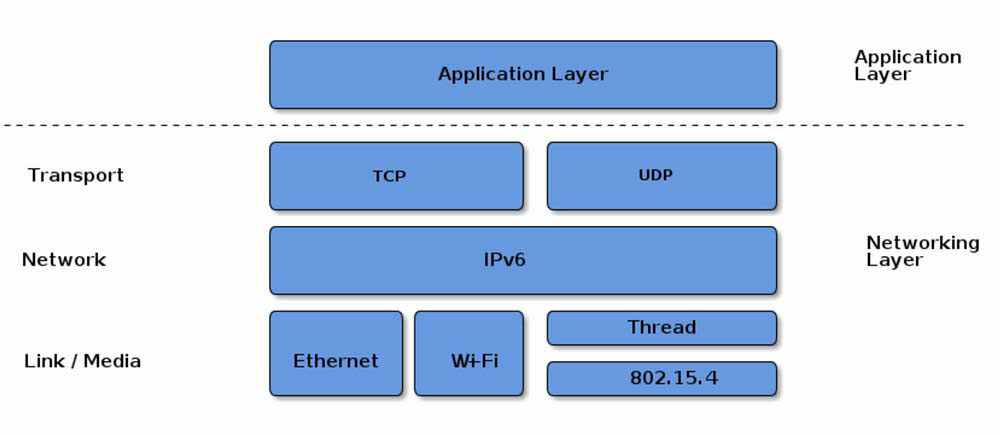
Matter provides a universal open-source abstracted application layer between the IPV6-based communication protocols in the transport layer and the device application software (Figure 1). The Matter software standard defines the various link layers needed to maintain interoperability.
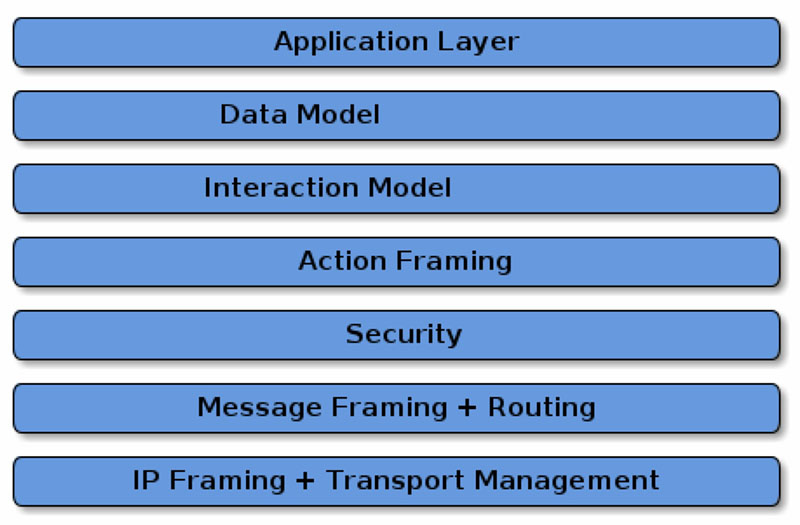
The Matter software suite architecture comprises six layers below the Application layer: Data Model, Interaction Model, Action Framing, Security, Message Framing and Routing, and IP Framing and Transport management (Figure 2).
The Application layer controls specific device functionality. For example, a thermostat application could include logic for monitoring the temperature and humidity, communicating with remote devices like handsets, and controlling heating and air conditioning systems.
The top layer of the Matter software suite is the Data Model layer, which includes the data and verb elements needed to support the Application. The Application uses those data structures to interact with the lower levels of the device software stack down through to the networking layer.
The Interaction Model layer includes the specific interactions that can take place between a server and client device, like reading or writing attributes on a server device that correspond to application behavior on the client. The Interaction Model works using the data structures defined in the Data Model.
The Action Framing layer takes the defined interactions and packages them in a binary format suitable for encoding and network transmission.
The Security layer encrypts the framed action message. It adds an authentication code to ensure that the receiver of the message can authenticate the data to maintain the confidentiality and accuracy of the communication.
The Message layer builds and formats the payload with the necessary header fields specifying the message properties and adds the routing information.
The payload is transferred to the transport protocol layer for IP management of the message. When the target device receives the message, the process is reversed, moving up through the layers until it has been formatted for use by the Application layer.
In addition to these layers, the Matter software suite includes specifications for establishing secure communication based on operational certificates or passcodes, setting up group communications and a bulk data transfer protocol for sending bulk data between nodes, and the option for defining manufacturer- or device-specific protocols. In addition to the Matter software, stacks on individual devices, controllers, bridges, and border routers are used to construct a Matter network.
Matter controllers
Matter is IP-based and forms local networks using Wi-Fi, Ethernet, and Thread. A Matter controller, sometimes called a hub, enables local Wi-Fi- and Ethernet-based Matter networks to access the Internet supporting remote access to Matter devices.
Existing devices, especially those from Amazon and Google, and some smart home hubs like SmartThings, can receive software updates enabling them to be Matter controllers. Devices with communications abilities independent of Matter, like a Wi-Fi smart thermostat with cloud support from the maker, will still be able to use their native remote-control functions without a Matter controller. Matter is designed to coexist with any manufacturer-provided functionality.
Matter bridges
Matter controllers connect Matter networks with the Internet, while Matter bridges connect Matter networks with other local wireless networks. For example, the Philips Hue Hub can be updated to become Matter compatible. When that is done, the Philips Hue smart lighting network can be linked to the local Matter ecosystem.
With a Matter bridge, the individual nodes, like the lights and accessories in a Philips Hue system, will not become directly Matter compatible. Still, they will operate through the bridge and work harmoniously with the Matter network. Bridges are expected to facilitate the adoption of Matter by enabling nearly any other local network to become Matter compatible, even if the individual nodes are not.
Border routers and Thread
Thread devices and networks are a special case. Thread is a low-power IEEE 802.15.4 IP-based wireless protocol that uses the same frequency Zigbee smart home devices. A border router is designed to communicate directly with Thread devices and connect them with a Matter network. Border routers can link multiple networks and control devices and include an integrated device interface for smart home controls. This is another place that can be confusing: Matter Thread border routers, like Matter controllers, are sometimes called Matter hubs. When a device is called a Matter hub, it’s important to clarify whether it’s a border router or a controller.
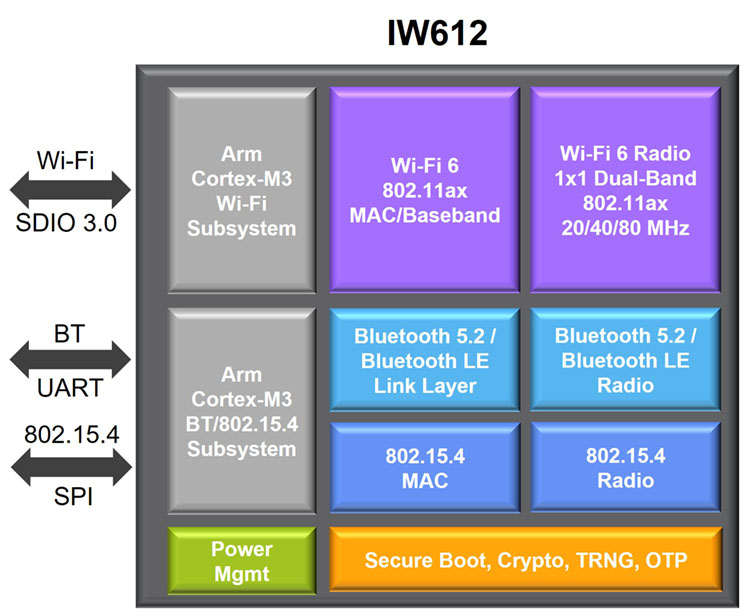
Border routers support integrating very low-power Thread devices like motion, door, and window sensors into a Matter network. Updating a device to become a Matter Thread border router is more complicated than updating a device to become a Matter controller. That’s because Thread uses IEEE 802.15.4, that’s incompatible with Wi-Fi. Recently, manufacturers have begun making tri-radio devices that support Wi-Fi 6, Bluetooth 5.2, and 802.15.4 and enable the design of border routers and other Matter devices (Figure 3).
Matters of security
Improved network security is a major element of Matter. It encompasses five properties:
Comprehensive – The layered security structure with authentication and attestation for commissioning, protecting every message, and securing over-the-air firmware updates are designed to support comprehensive functional security. Security is independent of the communication protocol that Matter runs on top of. Features like device libraries and application clusters are defined on top of Matter’s core specification. The open-source nature of Matter simplifies security integration and supports interoperability across device types and manufacturers. In addition, Matter uses standard passcode-based session and certificate-based protocols to establish secure sessions for onboarding, attestation, and operation. No device can be added to a Matter network until proven genuine. To guarantee a uniform and compliant ecosystem, Matter also includes the Cloud Security Alliance (CSA) Distributed Compliance Ledger technology in Matter devices to ensure uniform and compliant networks and support worldwide interoperability that enables Matter commissioner devices to check and make sure that devices have been Matter certified.
Strength – Matter employs a variety of techniques to strengthen security. Advanced Encryption Standard (AES) in Cipher Block Chaining-Message Authentication Code (CCM) mode is used for confidentiality and integrity with 128-bit keys. AES in counter (CTR) mode preserves privacy by protecting identifiers. Secure hash algorithm 256 (SHA-256) ensures integrity, and elliptical curve cryptography (ECC) with the ‘secp256r1’ curve is used for digital signatures and key exchanges, standard key derivation schemes, and random number generators.
Ease of use – While it’s both comprehensive and strong, Matter security is designed to be easy to integrate into devices and easy for consumers to use. Test vectors and examples for each aspect of functional security are included in the Matter core specification. Reference implementations are available to Matter designers on the GitHub repository, along with a modular implementation of Matter functional security. Examples are included for alternative integration of hardware security modules (HSMs). Security in Matter devices is designed to be invisible to users; it automatically works without user intervention.
Resilience – Matter security is designed to detect, protect and recover and it provides multiple ways to perform some operations. For instance, if a secure session cannot be established using a short resumption protocol, the full resumption protocol is used. Matter includes a sophisticated message counter algorithm to support resilience to denial-of-service attacks. It has been defined as resilient even when involving sleeping devices or group communications.
Agility – All cryptographic primitives are abstracted in the Matter core specification, leaving the option for revisions that adopt new cryptographic primitives without having to rewrite the basic specification. Flexibility and agility are further enhanced by the modular design of the Matter software suite enabling some of the modules to be replaced and upgraded to address future developments in security risks and threat analysis.
Summary
Matter is a new interoperable application layer software suite for wireless IoT devices. A Matter network can include bridges, controllers, border routers, and security, including authentication and cloud connectivity. It can also link Amazon AWS, Google, and Microsoft networks into a seamless user experience. Only recently have tri-radio ICs been introduced that can support Matter bridges, controllers, and border routers.
References
Connectivity and Matter, NXP
Matter Specification, Connectivity Standards Alliance
What is Matter?, Google Home Developer Center