 Crypto Quantique announces a post-quantum computing (PQC) version of its QuarkLink chip-to-cloud IoT security platform. The upgraded platform is believed to be the first to use post-quantum algorithms recently announced for standardization by the National Institute of Standards and Technology (NIST), particularly the chosen key encapsulation mechanism (KEM), CRYSTALS-Kyber.
Crypto Quantique announces a post-quantum computing (PQC) version of its QuarkLink chip-to-cloud IoT security platform. The upgraded platform is believed to be the first to use post-quantum algorithms recently announced for standardization by the National Institute of Standards and Technology (NIST), particularly the chosen key encapsulation mechanism (KEM), CRYSTALS-Kyber.As part of its recent announcement on post-quantum standards, NIST focused on the applicability of the schemes to embedded devices, including benchmarks of all schemes on the ARM-Cortex M4, demonstrating that post-quantum security on the IoT is a realistic goal. Elsewhere, NIST standardized multiple signature schemes, including both lattice- and hash-based signatures, and suggested algorithms of a future interest that may be standardized later. Crypto Quantique’s KEM-TLS protocol is designed to be flexible and can easily be adapted to these changing standards.
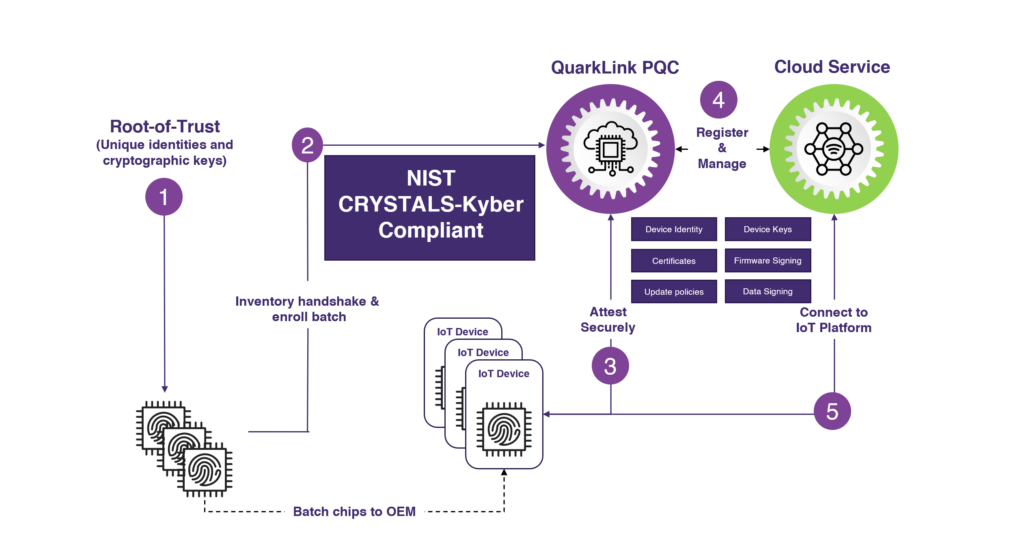
QuarkLink is a comprehensive platform for connecting IoT devices with an embedded root-of-trust to server-based applications. Its functions include device provisioning, automated secure onboarding to applications, and lifetime security management. Via a simple interface, users can achieve firmware encryption, signing and secure updates over the air, certificate and key renewal, and device revocation. A few keystrokes initiate an automated process for onboarding thousands of devices in minutes to a server platform, or to multiple platforms simultaneously. AWS, Microsoft, and Mosquito are among the cloud services currently supported.
Crypto Quantique worked on the post-quantum version of QuarkLink’s enrolment, relying on a custom, built-in-house variant of the novel KEM-TLS protocol developed by researchers at the Department of Computer science at ETH Zurich. The research was led by Professor Kenny Paterson. The resulting variant of the KEM-TLS protocol is particularly suited to the IoT setting, as its reliance on KEMs as opposed to post-quantum digital signatures lowers bandwidth costs and increases efficiency, without compromising security.