Many of the differences between RISC-V, ARM, and x86 microprocessors are subtle and relate to how memory is addressed, branches are executed, exceptions are handled, and so on. This article will consider higher-level differences and will briefly compare reduced instruction set computing (RISC) and complex instruction set computing (CISC), consider the impact those differences have on the tradeoff between power consumption and computing performance, look at how security and predicated execution are handled, how virtualization is implemented, and end with an overview of applications suitability for RISC-V, ARM, and x86 devices.
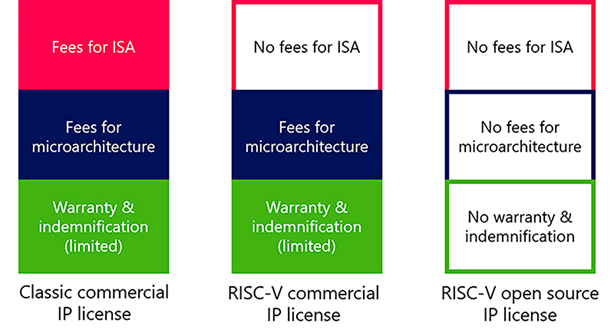
The x86 architecture from Intel is also offered on CPUs from AMD, ARM processors, and IP are offered by Arm Limited, and the RISC-V International organization is developing RISC-V. Two very significant differences between Intel, AMD, ARM, and RISC-V are in the business models and the computing architectures. Intel, AMD, and ARM are based on proprietary IP, and the companies sell and/or license their products. RISC-V is an open specification and platform; it is not an open-source processor. Open-source RISC-V cores are available, but there are also commercially licensed cores.
RISC-V and ARM processors are based on RISC concepts in terms of computing architectures, while x86 processors from Intel and AMD employ CISC designs.
RISC vs. CISC computing
A RISC architecture has simple instructions that can be executed in a single computer clock cycle. As a result, the completion of a specific task often requires the execution of multiple instructions. That same task could be completed with fewer instructions (or even a single instruction) on a CISC processor.
CISC computing seeks to complete a task in as few lines of code as possible. A single CISC instruction may take multiple computer clock cycles to complete. For example, multiplying two numbers of a CISC processor can be completed with a single instruction:
MUL 1200, 1201
“MUL” is a complex instruction. It does not require the programmer to explicitly use any call, loading, or storing functions. It operates directly on the computer’s memory and resembles a command in a higher-level programming language. Multiplication on a RISC processor cannot be completed with a single command; several simpler instructions are required to load each operand from specific locations in memory (1200 and 1201 in the example below), multiply the numbers, and then store the result:
Load A, 1200
Load B, 1201
MUL A, B
Store 1200, A
In this example, the Load instruction stores the data from memory locations 1200 and 1201 into registers A and B, respectively. The MUL instruction multiplies the values in the two registers. It saves the result in A, and the Store instruction stores A’s value in memory location 1200 (or any other specified memory location). In a RISC processor, operations such as MUL are only performed on registers, not directly on the memory. While this increases the instruction count, it enables the use of simpler instructions.
Power vs. Performance
Less power is consumed executing simpler RISC instructions compared with CISC instructions. CISC processors seek to minimize the number of instructions per program at the expense of the number of computer clock cycles per instruction. RISC takes the opposite approach, using simple instructions that can be executed in a single clock cycle at the cost of a higher number of instructions. The following equation shows the relationship between a computer’s performance capability (the time to run a program) and the cycles per instruction, and the number of instructions per program:
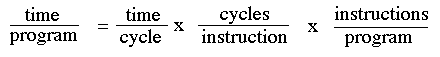
From this equation, there are two ways to improve performance, minimize the number of instructions per program or reduce the number of cycles per instruction. In general, the RISC approach is more successful in reducing overall power consumption, sometimes at the expense of lower performance. However, the lines of difference are narrowing. ARM has added more complex instructions to increase processor performance (at the expense of higher power consumption). Intel breaks down some of its opcodes into micro-ops that are RISC-like to achieve lower power consumption.
Security
Privilege rings (sometimes called protection rings) are hierarchical domains established to protect data and functionality from faults, improve fault tolerance, and improve security from malicious actions. Rings are set up in a hierarchy from most-privileged, or most trusted, to least-privileged, or least trusted. The zero ring is usually the most-privileged level and interacts directly with the CPU core and memory.
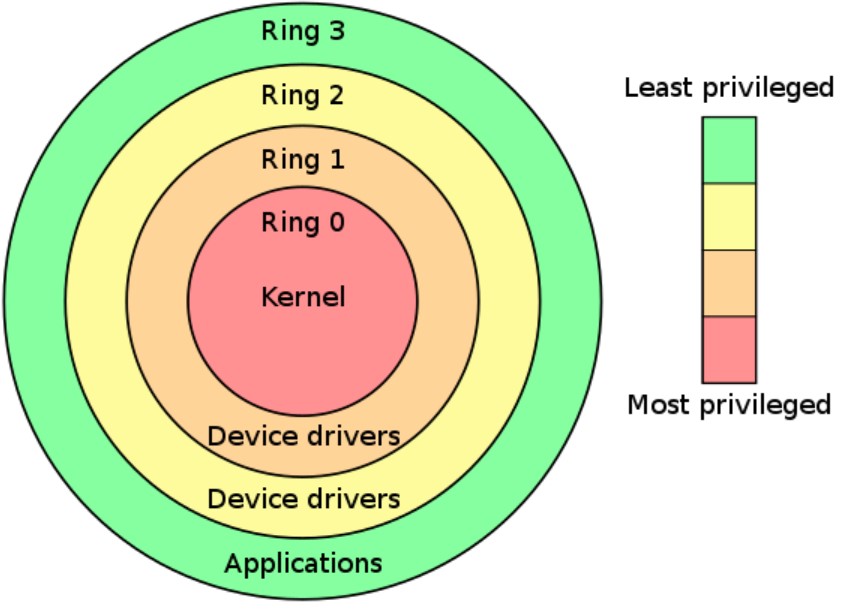
The x86 architecture includes four levels of privilege rings. The ARM v7 architecture includes three privilege levels; applications, operating system, and hypervisor. The concept of an isolation mechanism is used by both ARM and RISC-V. ARM employs hardware-based security where the domains are hard-coded into the hardware, while RISC-V uses software-defined isolation domains.
OP-TEE is an open source trusted execution environment (TEE) implementing the ARM TrustZone technology. OP-TEE has been ported to many ARM devices and platforms, including ARM v8. RISC-V MultiZone security software model is small, and therefore faster. Several security mechanisms are built into RISC-V, including four levels of privilege rings, secure interrupt processing, and a unique physical memory protection (PMP) mechanism. Commercially available security enhancements are also available for RISC-V, including cryptographic libraries, roots of trust, and multi-domain TEEs.
RISC-V’s open source nature results in transparency that proprietary ISAs lack and provides the possibility for another level of security. The RISC-V community is large and diverse, with many designers constantly studying the security environment and potential threat vectors. Once a security risk is identified, it is usually shared with the open community enabling experts to develop or propose solutions rapidly.
Predicated execution
Predicated execution allows some instructions only to execute if a specific previous condition is true. For example, a previous result must be greater than zero; otherwise, the processor moves on to the next instruction. ARM and x86 support various formats of predicated execution.
Macro-operation fusion is a hardware optimization technique where a series of adjacent macro-operations are merged into a single macro-operation before or during decoding. ARM supports a number of macro-op fusion operations in their recent microarchitectures. Micro-operation fusing merges two instructions into one inside the processor, effectively implementing predicated execution without the instruction set’s help.
The basic RISC-V instruction set does not support predicated execution. However, the experimental BOOMv3 out-of-order speculative RISC-V processor uses a combination of a reduced instruction set with micro-operation fusing to implement predicated execution.
Virtualization of CPUs, memory, and I/Os
ARM, x86, and RISC-V all support virtualization of CPUs and memory. The RISC-V ISA does not currently support the virtualization of I/Os. In the x86 ecosystem, Intel and AMD have their own virtualization approaches. Intel’s are called Virtualization Technologies or VT. VT is composed of VT-x, which encompasses the core side features; VT-d, which encompasses the input-output memory management unit (IOMMU); and VT-c, which covers the network interface. AMD offers core side virtualization under the label AMD-V, while the IOMMU is called AMD-Vi. The Intel and AMD offerings are different in implementation details but are more closely architected to each other than ARM’s offerings.
Virtualization extensions similar to the approach taken by the x86 processors have been added to the ARM architecture. The ARM virtualization extensions enable hardware means to virtualize a CPU using a hypervisor. Multiple operating systems can be run on each of the virtual CPUs.
The RISC-V H (hypervisor) extension v0.6.1 introduces a full duplicate of the CPU state: one copy for the guest and one copy for the host (similar to Intel VT-x). RISC-V supports the virtualization of CPUs by making sensitive registers and instructions privileged to host mode. As seen from the pre-release version number, RISC-V virtualization is a work in process. The first public implementation and evaluation was recently published of the latest version of the RISC-V hypervisor extension in a Rocket chip core for use in embedded systems.
Like the x86 and ARM architectures, RISC-V supports the virtualization of memory using multi-stage page tables. Also, RISC-V implements identical page table entry formats for both guest and host tables.
I/O virtualization is left to be specified in RISC-V. It will mostly be a feature of the IOMMU and the platform-level interrupt controller (PLIC), which lies outside the domain of the RISC-V ISA to specify. The PLIC, as currently specified, does not include registers for configuring the injection of interrupts.
RISC-V and ISA customization
RISC-V was engineered from the beginning to support not only the base ISA and standard extensions but it can also support custom ISA extensions. While ARM was not initially designed to use custom extensions, that is changing, and the ARM ecosystem is beginning to employ custom extensions. The x86 ecosystem is closed and does not generally support custom ISA extensions.
The RISC-V ISA is organized into groups of instructions (the base ISA & standard extensions). The ability to use extensions to the standard ISA can provide support for specific applications. For example, the recently released RISC-V Vector extension (RVV) enables processor cores based on the RISC-V ISA to process data arrays alongside traditional scalar operations to accelerate the computation of single instruction streams on large data sets. Examples of tasks suited for a vector processor include:
- Machine learning
- Compression both for images, zip files, etc
- Cryptography
- Multimedia: audio, video
- Speech and handwriting
- Parity checks, checksums
- Hash/joins
RISC-V ISA’s ability to support custom extensions can be a key differentiator for a specific use case or application. The use of custom extensions does not break compliance with the main ISA. Processors that support custom extensions can also run generic RISC-V software.
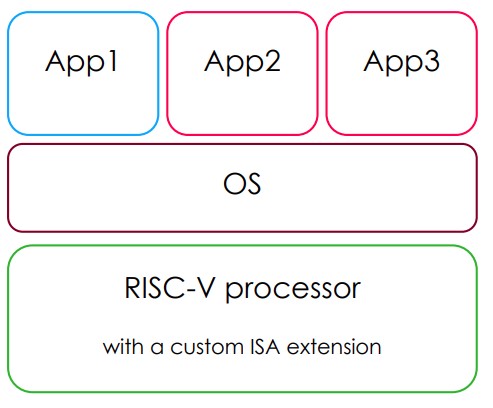
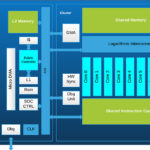
The figure above shows a custom ISA extension in a RISC-V software stack. The operating system (OS) can be a real-time OS (such as embOS, FreeRTOS, LynxOS, etc.), or a rich OS (such as Linux, Android, Windows, etc.). In this example, App1 does require performance enhancement and does not use the custom ISA extensions. It can comply with a standard compiler. App2 and App3 employ the custom ISA extensions to boost performance and must be complied using a complier that incorporates the custom ISA extensions.
Summary
The differences between x86, ARM, and RISC-V microprocessors are many and varied. Those differences drive general application suitability. x86 processors from AMD and Intel dominate in computers and servers. On tablets and smartphones, ARM processors from Apple and Qualcomm are dominant. ARM processors have also been strong in embedded applications. That strength is being challenged as RISC-V is increasingly used in embedded systems, automotive systems, disk drives, artificial intelligence, and machine learning applications.
References
A First Look at RISC-V Virtualization from an Embedded Systems Perspective, arxiv.org
Creating Domain-Specific Processors Using Custom RISC-V ISA Instructions, Codasip
Open Portable Trusted Execution Environment, OP-TEE organization
RISC-V, Wikipedia
RISC vs. CISC, Stanford University